
Building a Robust Security Stack
Your security stack is the foundation of your cybersecurity protection. Whether you’re building a stack from scratch or making updates and changes to your existing setup, it’s a task that needs to be done correctly and with cybersecurity best practices in mind.
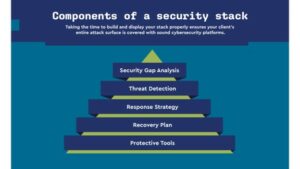
Determining your needs
The first step in properly building your security stack is assessing your needs. In general, there are six areas of business risk most organizations are likely to face:
- Network perimeter security. This is a business’s first line of defense. It concerns risks of initial threat detection, remediation, and hardening endpoint terminals.
- Internal security. Human error and data mismanagement can often lead to leaks or breaches from the inside. This usually happens when information is passed back and forth during internal communications. Internal security seeks to limit those occurrences and other internal threats – widely considered the most dangerous threat to cybersecurity.
- Physical security. This risk area concerns the security of a system’s software and hardware. Mitigating this risk involves cybersecurity frameworks like Access Control and Zero Trust.
- Incident response. No matter your cybersecurity setup, it won’t always offer 100% protection. How to respond to threats that get through the defenses is an integral part of a business’s risk and overall cybersecurity plan.
- Long-term response. Businesses also need to focus on learning and reporting after successful attacks. Cyber forensics and in-depth reporting of previous cyber threats provide the necessary knowledge to strengthen defenses moving forward.
- Cloud security. As the interest in cloud technology grows, so does the potential risk. 95% of security professionals have expressed some concern about the security of public cloud systems. This means that cloud security systems will need to keep pace as these environments become more complex.
Keep these six key areas in mind as you assess your current cybersecurity infrastructure and look for opportunities to optimize your security stack.
Essential tools for your security stack
One thing remains constant no matter how different security stacks can be. That constant is the fact that you need to use the right tools. As mentioned, it’s easy to become overwhelmed by the wealth of options and include too many tools when building your stack.
Here are five must-have tools when building your security stack (in alphabetical order):
- Cloud security posture management (CSPM)
- Endpoint detection and response (EDR) tools
- Mobile device management (MDM)
- Penetration testing capabilities
- Remote access platform
Building your cybersecurity stack effectively is a balancing act. In theory, it’s easy to assume that the more tools you include, the better your protection will be. While this is true to a point, there is a point of diminishing returns.
Along with that, adding too many tools can make your stack overly complex and, ultimately, leave your system open to vulnerabilities. The goal is to build an IT security stack that includes as many useful tools as possible but doesn’t take away from its primary purpose.
Are you interested in building a comprehensive security stack for your business? We’re here to help. Contact us today.